As Large Language Models (LLMs) become the backbone of modern AI applications, a silent challenge lurks beneath their capabilities—the protection of Personally Identifiable Information (PII). While traditional methods like masking names with
This blog explores a transformative approach to PII anonymization—one that swaps crude redactions for smart synthetic data generation. By using a multi-step pipeline powered by intelligent models, we maintain the natural flow of language while safeguarding sensitive information, offering a leap forward in both privacy and performance.

Why Basic Masking Falls Short in LLM Training
Handling PII in text requires more than basic redaction methods such as hash substitution (e.g., “Hello, my name is ####”) or entity-based placeholders (e.g., “Hello, my name is [PERSON_NAME]”).
Although these techniques remove sensitive data, they often produce unnatural text that disrupts readability and diminishes training effectiveness. This creates a fundamental challenge: how do we protect privacy without sacrificing the linguistic quality that makes training data valuable?
This study introduces a framework that goes beyond traditional masking by using models to detect, replace, and validate synthetic data substitutions. By preserving contextual relationships and semantic integrity, our method ensures that models trained on modified datasets remain effective while safeguarding privacy.
The Privacy-Utility Dilemma
Limitations of Conventional Privacy-Preserving Mechanisms
Research indicates that traditional PII obfuscation methods, such as masking, token substitution, and differential privacy, can negatively affect model performance. These approaches tend to raise perplexity, disrupt text coherence, and introduce inconsistencies that hinder learning. For example, evaluations have shown the following perplexity scores [1]:
- Baseline Model (ClearView OpenLlama 3B): Perplexity = 1.16
- Masked Data Model (OpenLlama 3): Perplexity = 2.83
- Differential Privacy (DPSGD, ε=1): Perplexity = 4.87
These results demonstrate that naïve privacy-preserving techniques can significantly inflate perplexity scores, limiting the model’s ability to learn effectively from training data.
The increased perplexity manifests particularly in under-represented groups, where utility degradation can be substantially worse compared to well-represented data points. In addition to the direct impact on perplexity, such methods also increase computational demands and may make models more vulnerable to adversarial attacks due to information loss and reduced model robustness.
This highlights the critical need for more sophisticated privacy-preserving techniques that can maintain model utility while providing robust privacy guarantees
Risk Factors in LLM Training
A major concern is that LLMs might memorize and inadvertently regenerate sensitive PII from their training data. While synthetic data techniques can help mitigate this risk, they do not entirely eliminate it [2]. Ensuring privacy requires a combination of robust anonymization techniques and ongoing monitoring to detect potential data leakage.
Empirical studies have shown that LLMs trained on inadequately sanitized datasets can inadvertently regurgitate personal identifiers, financial records, and contact details. The memorization capabilities of modern transformer architectures make them particularly susceptible to retaining and reproducing sensitive information, even from single training examples.
Addressing these vulnerabilities demands a methodical approach that preserves syntactic and semantic coherence while effectively obfuscating sensitive elements. This requires developing sophisticated anonymization frameworks that can maintain statistical properties and relationships within the data while removing privacy-sensitive information. The challenge is further complicated by the need to preserve the contextual relevance and linguistic structure that enables effective model learning. Moreover, risks extend beyond direct identifiers to quasi-identifiers, necessitating sophisticated, feature-aware anonymization strategies.
The challenge of privacy preservation must be balanced against the need for model utility. This balance becomes particularly critical in specialized domains where data utility is paramount but privacy concerns are equally important.
PII Protection Framework
Multi-Stage PII Obfuscation Pipeline
Our proposed framework integrates several computational models to identify, analyze, and replace PII while preserving linguistic coherence. Key features include real-time validation modules and context-aware entity substitution mechanisms that enhance context retention across diverse datasets002
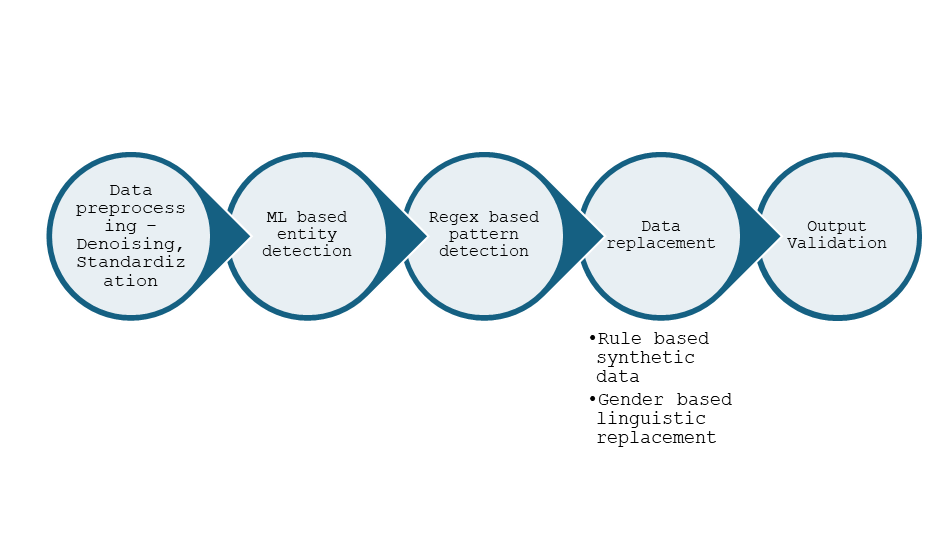
Data Preprocessing
In this phase, the framework first applies natural language processing techniques to cleanse the input text by removing extraneous artifacts, correcting typographical errors, and eliminating irrelevant symbols that can obscure contextual meaning. Simultaneously, standardization methods such as lowercasing, and punctuation harmonization ensure that the diverse inputs conform to a uniform format, which significantly improves the performance of downstream tasks like entity detection and synthetic data generation.
This dual approach not only reduces noise and enhances the quality of the data but also preserves the intrinsic linguistic and semantic structure, ultimately facilitating more accurate and context-aware PII replacement throughout the entire pipeline.
Entity Detection
The methodology incorporates models such as numind/NuExtract-v1.5 [3] for high-precision entity recognition in privacy-sensitive documents, representing a significant advancement in automated PII detection and handling. Compared to conventional Named Entity Recognition (NER) techniques, NuExtract demonstrates improved efficacy in detecting a wide range of PII within heterogeneous texts. In our current implementation, we leverage the pre-trained NuExtract model to accurately identify PII.
This streamlined approach ensures robust entity detection across diverse document types while maintaining the integrity of the anonymization process, with particular attention to preserving the semantic relationships and structural coherence of the original text The modular design of our system allows for easy integration of additional entity recognition models and synthetic data generators, providing flexibility to adapt to evolving privacy requirements and new types of sensitive information.
Rule-Based Pattern Detection
In addition to ML-based entity detection, rule-based techniques play an important role in identifying and replacing certain forms of PII that follow predictable patterns or formats. For instance:
- Regex-Based Detection of Structured PII: Social Security Numbers, phone numbers, email addresses, and other structured identifiers can be matched using regular expressions designed around fixed formats (e.g., XXX-XX-XXXX for SSNs).
- Custom Domain Rules: Depending on the domain, you may have additional identifiers (like employee IDs, shipment codes, or transaction IDs) with well-defined alphanumeric patterns. Hard-coded rules and look-up tables can quickly capture these fields.
Once an entity or pattern is recognized via these rules, deterministic replacements ensure repeat occurrences of the same PII element (e.g., the same SSN) map to the same synthetic value across the corpus. This step lays the groundwork for seamless integration with context-aware methods and the broader synthetic data generation process.
Synthetic Data Generation
Rather than applying simple masking, our framework leverages a sophisticated synthetic data generation approach that maintains the semantic structure and statistical properties of the original data.
Detected PII is replaced with synthetic values using predefined mappings that utilize the Faker [5] library, incorporating domain-specific rules and constraints to ensure the generated data maintains real-world plausibility
Additionally, regex-based methods are employed for specific patterns (e.g., Social Security Numbers and email addresses) to ensure consistent and accurate replacement.
This combined strategy preserves the structural and contextual integrity of the original text while effectively anonymizing sensitive information. The framework incorporates intelligent pattern recognition to handle complex cases where PII may be embedded within larger textual structures or span multiple formats, ensuring comprehensive coverage of sensitive data patterns. The architecture also includes extensive validation against diverse data to ensure reliable performance across various document types and content structures.
Context-Aware PII Replacement
To maintain fluency and logical consistency, the framework employs models like cross-encoder/nli-deberta-v3-base [4] for gender inference and contextual adjustment, representing a significant advancement in context-aware anonymization.
For instance, when replacing names, the system first predicts the gender of the original name using the zero-shot classifier and then generates a corresponding synthetic name via the Faker library ensuring consistency in the anonymized output.
This targeted replacement ensures that gender-based linguistic patterns are preserved, avoiding mismatches such as replacing “Sarah” with a typically male name, and helps maintain the natural flow and semantic coherence of the anonymized text. Additionally, the system maintains consistency across document collections by implementing a deterministic mapping for recurring entities, ensuring that the same original name is consistently replaced with the same synthetic name throughout the corpus.
Output Validation
Ensuring the anonymized text remains coherent, consistent, and free from residual PII. It starts with an automated scan (using regex or ML-based checks) to confirm that no high-risk identifiers remain and that each flagged entity has indeed been replaced.
Next, we verify grammatical structure and use semantic similarity checks to maintain intelligibility and contextual accuracy. In cases where the same PII appears multiple times, deterministic mapping is enforced for consistent replacements.
Finally, for sensitive or high-stakes data (e.g., legal or healthcare records), an optional human review ensures compliance and readability before any further use or model training.
Implementation Methodology
Processing Pipeline
- Data Preprocessing:
- Text normalization and tokenization using the model’s tokenizer.
- Initial cleaning to remove noise.
- Standardization to ensure compatibility with the pre-trained model.
- PII Detection and JSON Parsing:
- Primary detection using the pre-trained NuExtract-v1.5 model.
- Parsing of the JSON output from the entity detection model.
- Secondary verification using regex patterns for specific formats (e.g., Social Security Numbers and email addresses).
- Synthetic Data Replacement:
- Rule-based replacement that substitutes detected PII with synthetic values generated via the Faker library.
- Integrated gender classification (using cross-encoder/nli-deberta-v3-base) to ensure that names are replaced with gender-consistent synthetic names.
- Final Validation and Output:
- Review of the output text for overall coherence.
- Assessment of anonymized outputs for consistency prior to deployment.
Performance Analysis
Performance Implications
Our approach demonstrates significant improvements over traditional methods by:
- Preserving natural language patterns and relationships.
- Maintaining context and semantic consistency through targeted, rule-based substitutions.
- Reducing the disruptions is typically associated with basic masking techniques.
Privacy Guarantees
Although our method does not provide formal differential privacy guarantees, it offers robust practical protection by:
- Completely replacing sensitive information with synthetic values.
- Preserving underlying data patterns without exposing the original content.
- Consistently handling various types of sensitive information through a unified replacement strategy.
Case Study: Applying the Framework
Consider the following example:
Original Text: "John Doe placed an order with order number 987654. His SSN is 123-45-6789, and his email is johndoe@example.com."
Masked Output Using Traditional Methods:
"[PERSON_NAME] placed an order with order number #######. His SSN is ###-##-####, and his email is [EMAIL]."
Our Approach:
"Michael Smith placed an order with order number 298374. His SSN is 832-29-4829, and his email is michael.smith@fakemail.com."
Unlike traditional masking, our approach generates human-like substitutions that retain the sentence structure and meaning.
Conclusion
Traditional masking techniques for PII protection often degrade text quality and reduce LLM training effectiveness. Our approach leverages advanced entity recognition, context-aware replacements, and synthetic data generation to preserve both privacy and data utility. By integrating machine learning–based validation steps, we ensure that anonymized datasets remain coherent and useful for downstream applications.
As AI models continue to evolve, refining these privacy-preserving techniques will be essential for ethical and responsible development.











